取消
自定義
為什麼要使用DesignCap製作PPT

模板多樣
在這裡,你可以找到各種類型的模板,包括業務介紹PPT模板、市場營銷PPT模板、公司簡介PPT模板等等。

資源豐富
DesignCap提供大量資源幫助你設計精美的PPT,包括庫存圖片、矢量圖、模塊、剪貼畫、圖形等等。

功能強大
DesignCap為你提供強大的編輯工具。只需點擊幾下滑鼠,就能把你的想法變為精美的PPT。

便宜好用
無須擔心預算問題。 DesignCap 提供了大量的資源供你免費使用。
如何在三步之內製作一個PPT
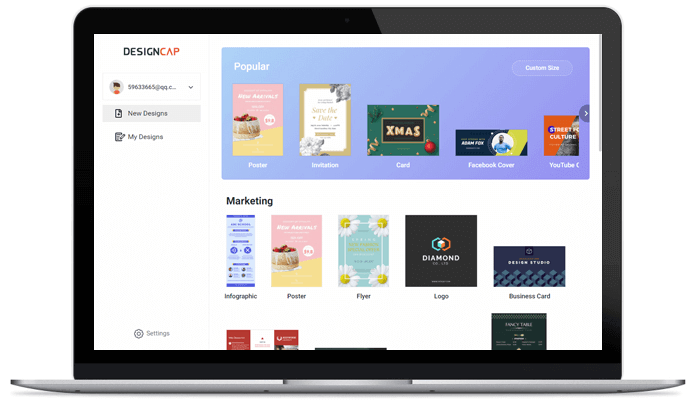
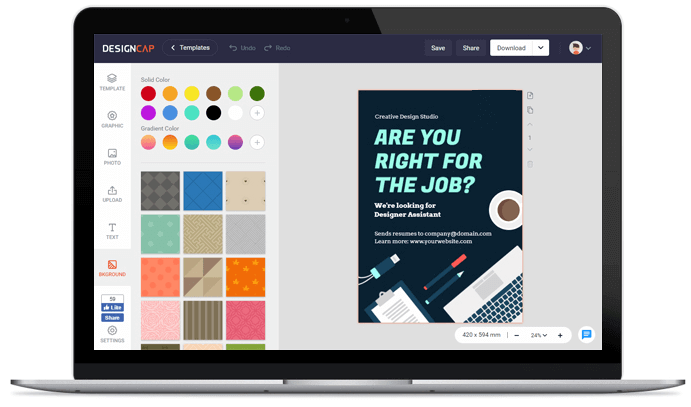

1. 選擇範本
選擇一個PPT模板然後開始製作。
2. 自定義
使用強大的編輯工具重新編輯PPT模板。
3. 輸出
將你製作的PPT下載到電腦或線上分享給其他人。
用戶評價

DesignCap 是一個可以簡單設計製作海報的線上工具有著各種不同類型、數百種的設計模版可依欲製作的海報主題類型選擇對應的模版, 不論是學生或是小本經營的店家都很適用。


DesignCap是一款平面設計好幫手,可以套用內建範本快速生成各種類型的海報,也能自行修改內容。


操作介面會看見很多樣版模組可以使用,文字等都可以做更換十分方便!功能支援夠大多使用者需求。










