Einflussreiche Templates für Instagram Posts
-
VorschauAnpassung
 Werbung Post
Werbung Post
-
VorschauAnpassung
 Agenten Post
Agenten Post
-
VorschauAnpassung
 Natur Post
Natur Post
-
VorschauAnpassung
 Party Post
Party Post
-
VorschauAnpassung
 Reise Post
Reise Post
-
VorschauAnpassung
 Café Post
Café Post
-
VorschauAnpassung
 Festival Post
Festival Post
-
VorschauAnpassung
 Zitat Post
Zitat Post
DesignCap’s Funktions-Highlights

Ästhetische Vorlagen
DesignCap’s Instagram Beiträge Generator bietet Ihnen stets professionelle Vorlagen. Alles ist anpassungsfähig.

Unzählige Elemente
Tausende professionell gestaltete Schriftarten, Formen und Symbole in der Mediathek werden Ihre Kreativität gestalten.

Einfache Nutzung
Ungeachtet Ihrer Erfahrung können Sie innerhalb weniger Klicks Bearbeitungen vornehmen.

Gutes Schnäppchen
Machen Sie sich keine Sorge um das Budget. DesignCap bietet kostenlose Ressourcen.
Gestalten Sie ein Instagram Beiträge in nur 3 Schritten
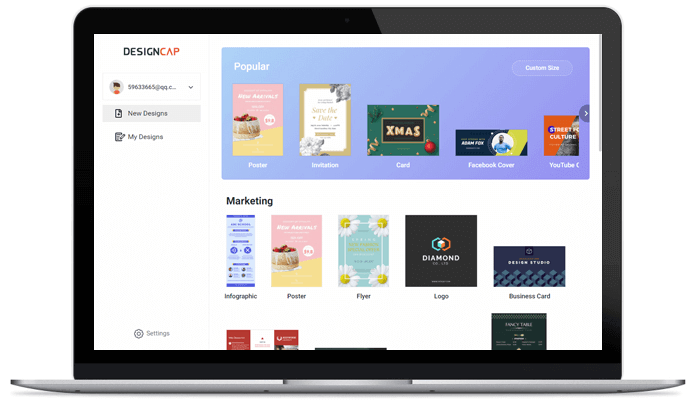
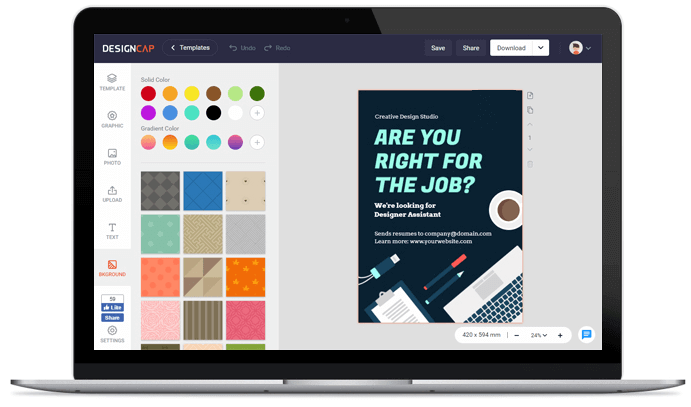

Wählen Sie zu Beginn ein Design aus den Instagram Beiträge Vorlagen.
Passen Sie Ihr Instagram Beiträge mit einfachen, aber leistungsstarken Bearbeitungswerkzeugen an.
Speichern Sie Ihr Instagram Beiträge auf Ihrem Computer oder teilen Sie es online.
Benutzerkommentar

hier können Sie komplette Werbeflyer / Poster im Handumdrehen online erstellen, und ist komplett individuell anpassbar.


Individuelle Poster kostenfrei in einer Minute erstellen, das verspricht DesignCap mit dem Online-Postermaker.


Spart euch die Kosten für eine Grafikagentur! Der einfach zu bedienende Editor erlaubt selbst Anfängern innerhalb von Minuten ein persönliches Poster oder einen Flyer.


