Una colección seleccionada de plantillas de historias de Instagram
-
PrevisualizarPersonaliza
 Cuaderno De Fotos De Otoño
Cuaderno De Fotos De Otoño
-
PrevisualizarPersonaliza
 Collage De Bebé
Collage De Bebé
-
PrevisualizarPersonaliza
 Bingo De Alimentos
Bingo De Alimentos
-
PrevisualizarPersonaliza
 Gran Inauguración
Gran Inauguración
-
PrevisualizarPersonaliza
 Collage De Viajes
Collage De Viajes
-
PrevisualizarPersonaliza
 Historia De Boda
Historia De Boda
-
PrevisualizarPersonaliza
 Cafetería
Cafetería
-
PrevisualizarPersonaliza
 Lección Práctica
Lección Práctica
-
PrevisualizarPersonaliza
 Esto O Aquello
Esto O Aquello
-
PrevisualizarPersonaliza
 Trabajar Desde Casa
Trabajar Desde Casa
-
PrevisualizarPersonaliza
 Diseño De Interiores
Diseño De Interiores
-
PrevisualizarPersonaliza
 Tienda De Moda
Tienda De Moda
Por qué elegir el creador de historias de Instagram DesignCap

Plantillas personalizables
Explora plantillas de historias de Instagram prediseñadas que puedes usar para diseñar una bonita historia de Instagram como un influencer en segundos.

Enorme archivo de fotos
Tienes acceso gratuito a nuestro archivo con millones de fotos. Examina la galería fotográfica y encuentra las fotos que se adapten a tu estilo.

Elementos de moda
DesignCap te ofrece numerosos recursos para embellecer tus diseños de historias de Instagram, como formas abstractas, patrones vintage y decoraciones modernas.

Tipogafía elegante
Los preajustes de tipografía listos para usar te ahorrarán mucho tiempo y te ayudarán a transmitir tu mensaje de una manera especial.
Cómo crear una historia de Instagram en 3 pasos
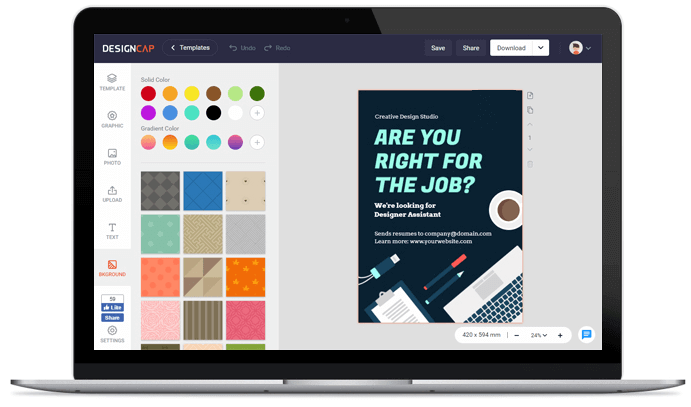

Elige una plantilla de historia de Instagram o diséñala desde cero.
Personaliza tu historia de Instagram con abundantes recursos artísticos y potentes herramientas de edición.
Descarga y comparte tu historia de Instagram personalizada.
Comentario de usuario

DesignCap te permite diseñar carteles, pósteres y flyers con la ayuda de sus plantillas, que podrás personalizar a placer.


DesignCap es una herramienta en línea, completamente gratuita, dedicada a ayudar a las personas a crear sus propios carteles y pósters.


DesignCap ofrece muchas herramientas de edición para sus necesidades de personalización, como la aplicación de efectos, importar nuestras propias imágenes, etc.


