...
Categories
Chart
Bar
Pie
Table
Sitemap
Swot Analysis
Area
Flowchart
Line
Map
Column
Organizational
Venn Diagram
Card
Wedding
Baby
Easter
Anniversary
Graduation
Greeting
Congratulations
Thank You
Valentines Day
Birthday
Halloween
Mothers Day
Thanksgiving
Fathers Day
Invitation
Business
New Year
Christmas
Halloween
Fathers Day
Baby Shower
Christening
Mothers Day
Thanksgiving
Engagement
Graduation
Party
Easter
Anniversary
Poster
Birthday
Music
Travel
Movie
Animal & Pet
Party
Motivational
Environmental Protection
Industrial
Fashion & Beauty
Kids
Non-profit
Exhibition
Law & Politics
Art & Entertainment
Sale
Holiday & Event
Business
Coronavirus
Sports & Fitness
Search: {{local.search_error_key}}
Search: {{local.search_subcategory}} in {{local.search_category}}
Sorry, no matches found. Please try again with different words or browse through our most popular templates.
Preview
Customize
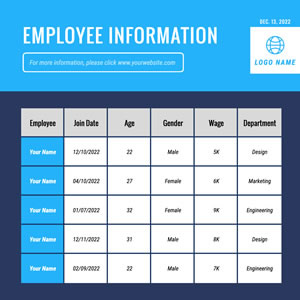
Employee Information Table
Preview
Customize
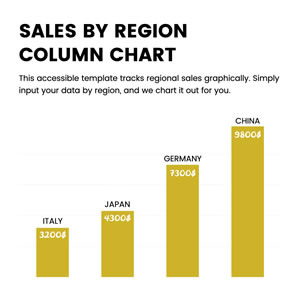
Sales by Region Column Chart
Preview
Customize
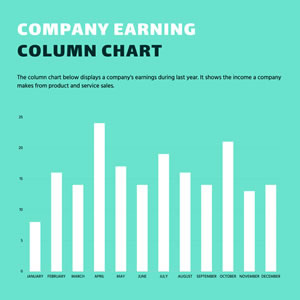
Company Earning Column Chart
Preview
Customize
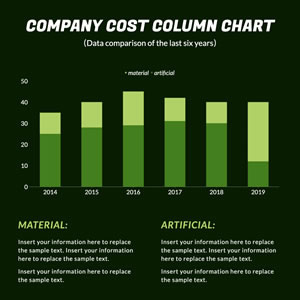
Company Cost Column Chart
Preview
Customize
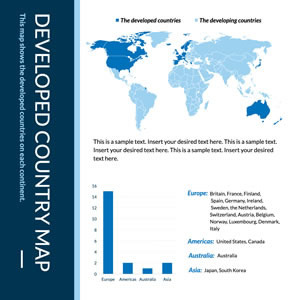
Developed Country Map
Preview
Customize
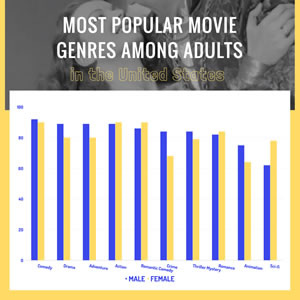
Favorite Type of Movie Column Chart
Preview
Customize
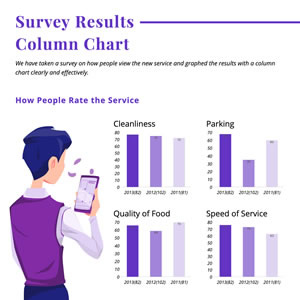
Survey Results Column Chart
Preview
Customize
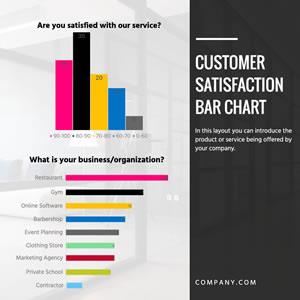
Customer Satisfaction Bar Chart
Preview
Customize
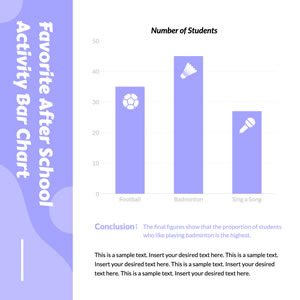
Favorite after School Activity Bar Chart
Preview
Customize
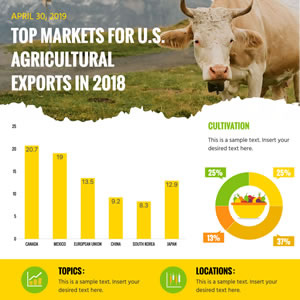
Agriculture Exports Column Chart
Preview
Customize
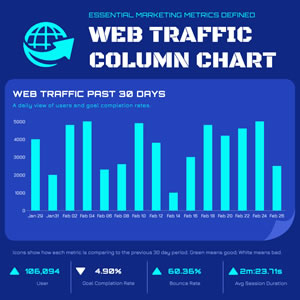
Web Traffic Column Chart
Preview
Customize
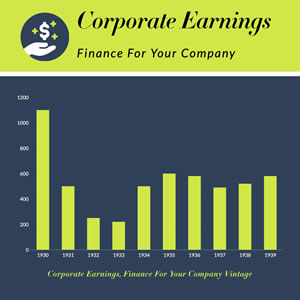
Corporate Earning Column Chart
Preview
Customize
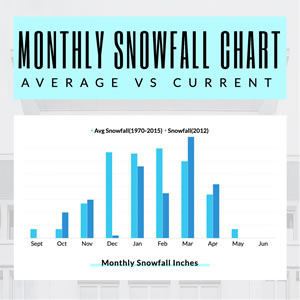
Monthly Snowfall Column Chart
Preview
Customize
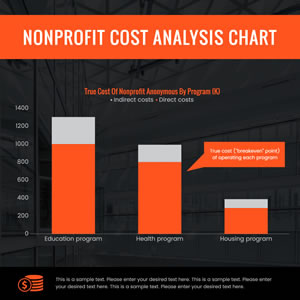
Nonprofit Cost Column Chart
Preview
Customize
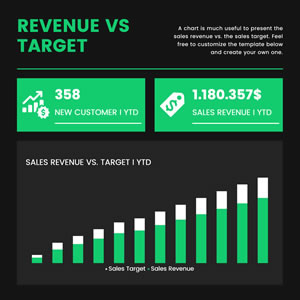
Sales Revenue and Target Column Chart
Preview
Customize
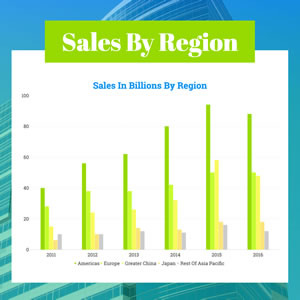
Regional Sales Revenue Column Chart
Preview
Customize
Hours of Television Watched Bar Chart
Preview
Customize
Company Earning Snapshot Column Chart
Preview
Customize
Financial Highlights Column Chart
Preview
Customize
Vehicle Sales Column Chart
Preview
Customize
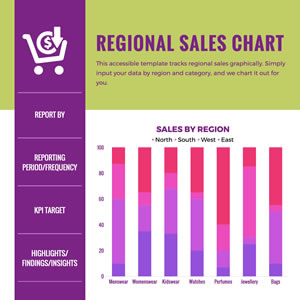
Regional Sales Column Chart
Preview
Customize
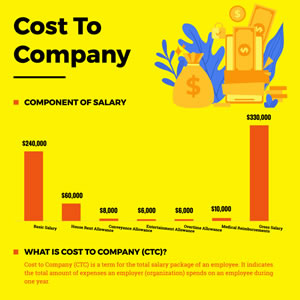
Cost to Company Column Chart
Preview
Customize
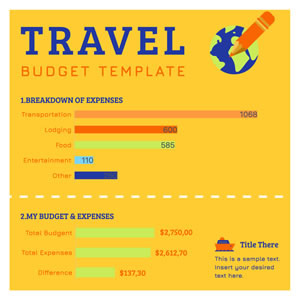
Travel Expenses Column Chart
Preview
Customize
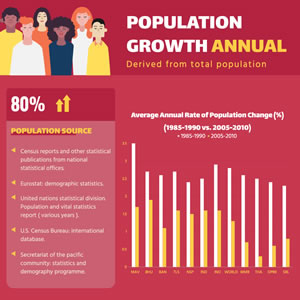
Annual Population Growth Column Chart
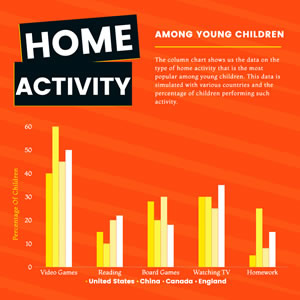
Preview
Customize
Home Activity Column Chart
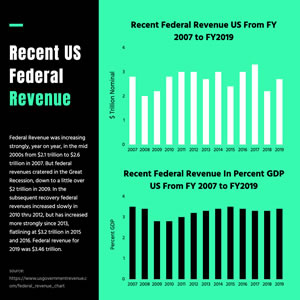
Preview
Customize
Federal Revenue Column Chart
Cancel
Customize
